Security
Spiral is designed with security as a core principle, implementing defense-in-depth strategies across authentication, authorization, encryption, and data protection.
Architecture
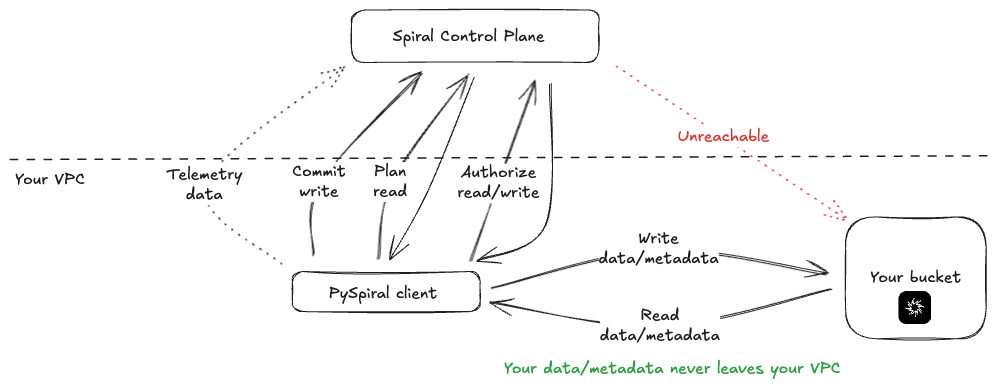
Spiral Tables are designed in such way that your data never leaves your VPC. The only exception are key columns. Spiral stores key schema for each table, which includes key column names, and tracks fragments which include key column stats, such as min/max values. PySpiral, Spiral client library, runs in your VPC and can access your bucket, but it is not authorized to read from the bucket. Spiral, control plane, provides temporary authorization for each read / write operation to PySpiral via signed URLs.
Authentication
Spiral supports multiple authentication mechanisms to integrate with your existing infrastructure.
OIDC Integrations
Spiral integrates with several OIDC (OpenID Connect) identity providers for seamless workload authentication:
- GCP - Google Cloud service accounts
- Modal - Serverless platform integration
- AWS - AWS IAM roles (coming soon)
See OIDC Integrations for detailed setup instructions.
SSO (Single Sign-On)
Enterprise organizations can configure SSO through WorkOS, enabling:
- SAML and OIDC-based enterprise SSO
- Domain-verified automatic user provisioning
- Centralized identity management
Authorization
Spiral implements role-based access control (RBAC) with fine-grained permissions. See Authorization for complete details.
Hierarchy
Access is controlled at two levels:
- Organization level - Manages membership and project creation
- Project level - Controls access to tables, indexes, and file systems
Roles
| Role | Project Access |
|---|---|
| Admin | Full access including grant management |
| Editor | Read/write access to all resources |
| Viewer | Read-only access |
Principals
Grants can be assigned to various principal types:
- Users and user groups
- Organizations and teams
- Workloads (service accounts, GitHub Actions, Modal apps)
Use OIDC-based workload authentication instead of static API keys whenever possible. This eliminates the need to manage and rotate secrets.
Encryption
Encryption in Transit
All communication with Spiral is encrypted using TLS 1.2 or higher:
- HTTPS only - All API endpoints require TLS
- Modern cipher suites - Using industry-standard encryption
- Certificate validation - Web PKI root certificate verification
Encryption at Rest
Data stored in Spiral is protected at rest:
- Object storage encryption - Data files are encrypted by the underlying cloud storage (S3, GCS, Azure Blob)
- Database encryption - Metadata is encrypted at rest in the database layer
Data Protection
Multi-Tenant Isolation
Spiral provides strong isolation between tenants:
- Organization boundaries - Data is isolated at the organization level
- Project scoping - All operations are scoped to authorized projects
Network Security
API Security
- Rate limiting - Protection against abuse
- Request validation - All inputs are validated before processing
- CORS configuration - Controlled cross-origin access
Compliance
Spiral is designed to help you meet compliance requirements:
- Data residency - Control where your data is stored
- Access controls - Fine-grained RBAC for compliance with least-privilege principles
- Audit trails - Logging for compliance and forensics
Contact us for specific compliance requirements including SOC 2, HIPAA, or GDPR.
Security Best Practices
For Administrators
- Use SSO - Enable SSO for your organization when possible
- Principle of least privilege - Grant only the minimum necessary permissions
- Regular access reviews - Periodically review and revoke unnecessary grants
- Use workload identity - Prefer OIDC over static credentials
For Developers
- Use OIDC authentication - Avoid storing API keys in code or configuration
- Scope access appropriately - Request only the permissions your workload needs
- Rotate credentials - If using API keys, rotate them regularly
- Secure your environment - Protect the environment where Spiral credentials are used
Reporting Security Issues
If you discover a security vulnerability in Spiral, please report it responsibly:
- Email: security@spiraldb.com
- Include details about the vulnerability and steps to reproduce
We take all security reports seriously and will respond promptly.